Featured
Table of Contents
- – How Does A Vpn Work? Tutorial For Beginners
- – What Is A Vpn?
- – What Is A Vpn And Why Should You Use One?
- – What Is A Business Vpn? │ Business Vpn Uses A...
- – What Is A Vpn? Virtual Private Network Tutorial
- – What Is A Vpn And How Does It Work?
- – Why You Need A Vpn, And How To Choose The Ri...
- – What Is A Vpn & How Does It Work?
How Does A Vpn Work? Tutorial For Beginners
In a mobile VPN, the server still sits at the edge of the organization's network, making it possible for secure tunneled gain access to by confirmed, authorized clients. Mobile VPN tunnels are not tied to physical IP addresses.
Hardware VPNs provide a number of benefits over software-based VPNs. In addition to offering boosted security, hardware VPNs can provide load balancing for big client loads. Administration is handled through a web internet browser user interface. A hardware VPN is more pricey than a software-based one. Since of the cost, hardware VPNs are more feasible for bigger services.

Paid supplier choices tend to be recommended more typically than complimentary ones. Some VPNvendors, among many, consist of the following: consists of a strong collection of security functions with a large collection of servers. Nord, VPN has functions such as Tor browser connections for confidential web surfing, while preserving a strong position on client privacy.
What Is A Vpn?
It does not use excessive in terms of extra functions and personal privacy tools, however. Still, it is usually thought about an excellent VPN service. is a VPN service with a big and diverse set of dispersed servers. It has strong privacy and details practices concentrated on security and provides additional functions such as split tunneling.
VPNs are legal in the United States, however users and companies should inspect if they are legal in particular nations. Numerous VPNs offer extremely similar technologies, so it can be difficult to pick which VPN will work best. Paid VPN services tend to be more relied on and include more security functions.
Around 2017, web users in the United States learned that ISPs might collect and offer their browsing history, and net neutrality ended up being a principle residents had to defend-- and effectively lost. An expense was passed by the U.S. Legislature in 2019 to revive net neutrality, but was eventually obstructed by the Senate.
What Is A Vpn And Why Should You Use One?
With this knowledge, making use of VPNs became a more legitimate requirement for people.
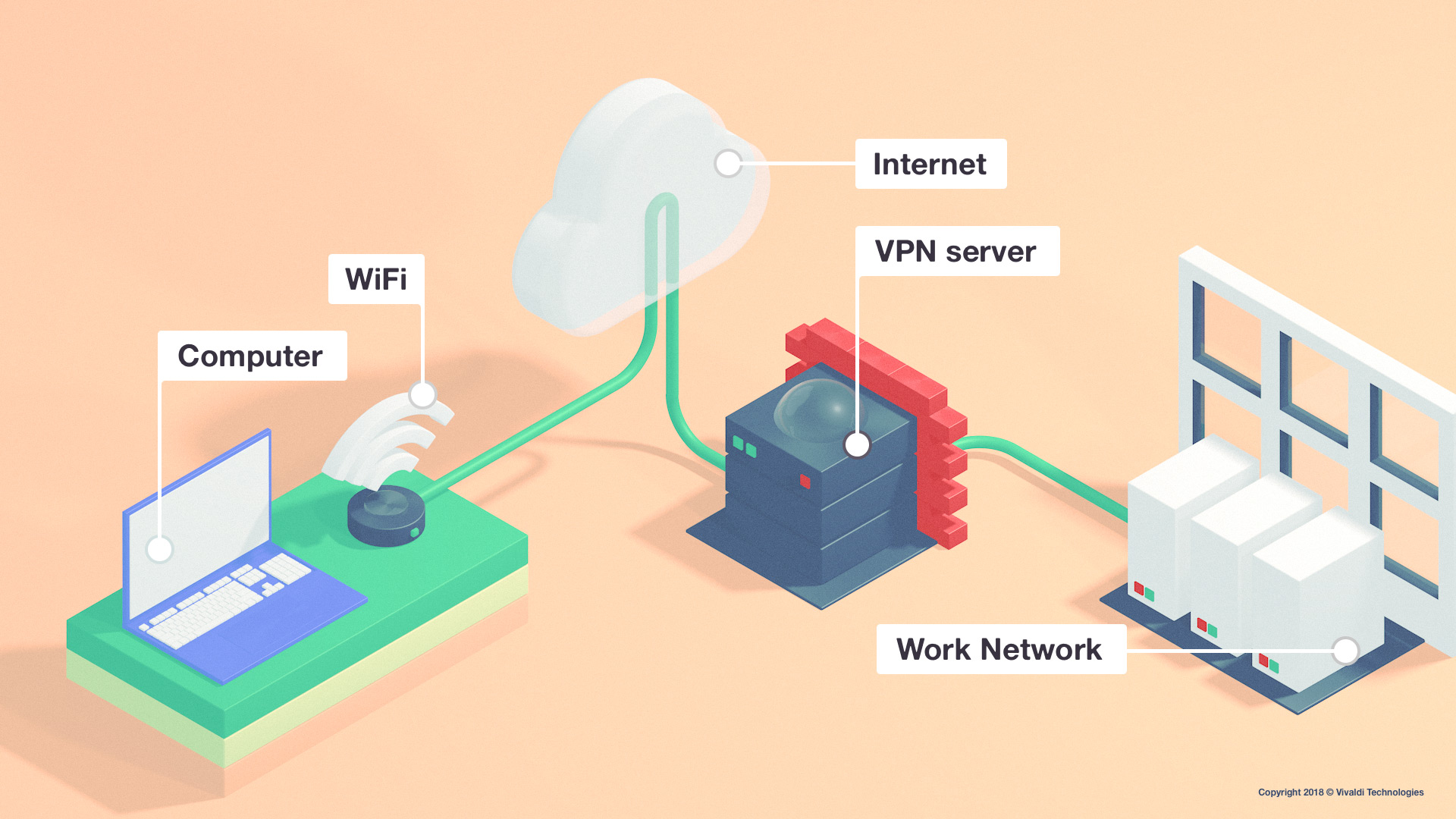
A VPN reroutes your traffic through a remote server, encrypting it while doing so. Usually, when you attempt to access a website, your ISP (Web Service Provider) gets the demand and redirects you to your location. When you link to a VPN, it redirects your web traffic through a remote server before sending it over to your location.
A number of years back, the most typical method to link computer systems in between numerous offices was by utilizing a rented line. Leased lines, such as ISDN (integrated services digital network, 128 Kbps), are personal network connections that a telecom company can rent to its customers.
What Is A Business Vpn? │ Business Vpn Uses And ...
These connections form a single wide-area network (WAN) for the business. Rented lines are trusted and safe and secure, the leases are pricey, with costs rising as the range between workplaces increases. Today, the internet is more accessible than ever before, and web service suppliers (ISPs) continue to establish faster and more reputable services at lower expenses than rented lines.
Paid VPN services operate really much like business VPNs but go through a VPN provider to reach the web, rather than through a private business. These services are incredibly easy to utilize. All you need to do is download the software, install it on your gadget, and connect to the server of your option.
Let's explore an example that explains how a VPN compares to other networking options.
What Is A Vpn? Virtual Private Network Tutorial
All your web traffic is routed through this tunnel to the server, which then sends the traffic off to the general public web as typical. Data returning to your gadget makes the same trip: from the internet, to the VPN server, through the encrypted connection, and back to your device.
There are a couple of choices out there to set up your own, such as Overview. Doing so is fairly uncomplicated, but you'll either need to maintain a server or lease one, which is less easy. While there are some efforts to make self-hosted VPNs more accessible, it's something best left to tinkerers who aspire to get their hands (digitally) dirty.
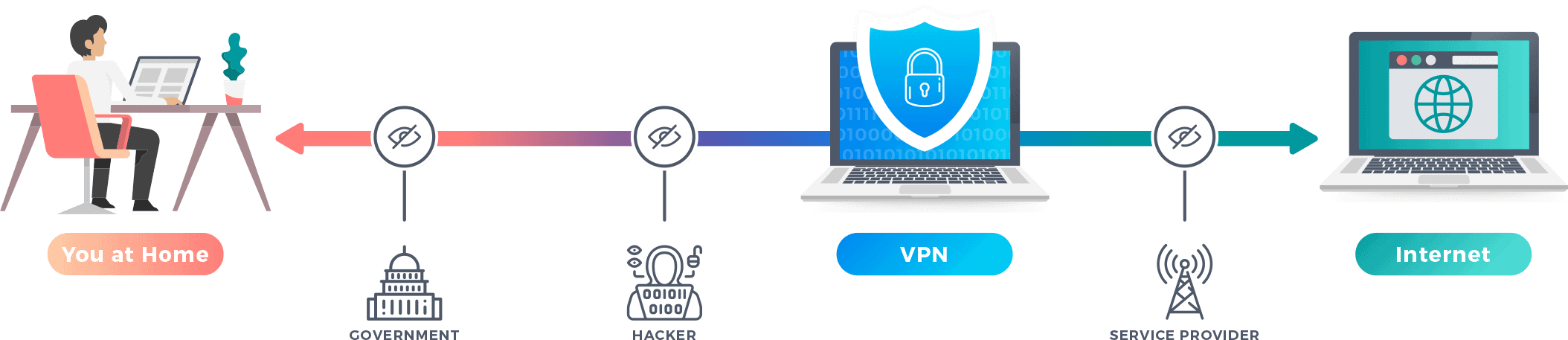
If you do not like that a company you're already paying is profiting from your information or if you have concerns about ISPs hoarding detailed information about your activities, a VPN will assist. Not even your ISP can see your web traffic when you use a VPN.VPNs also make it harder for marketers and others to track you online.
What Is A Vpn And How Does It Work?
When the VPN is active, your true IP address is concealed, and anyone watching you can only see the IP address of the VPN server. By concealing your real IP address, VPNs reject snoops one tool used to identify and track you online. Regardless of that, VPNs do not make you fully confidential online.

Some VPN services include committed antivirus tools as well, and some anti-viruses business now use VPNs. We don't normally check the malware-detecting capabilities of VPNs, since we see VPNs mainly as a privacy service.
A VPN will conceal the contents of your web traffic from some observers and can make it harder for you to be tracked online. However a VPN can, at best, supply just limited protection versus the dangers you're probably to come across on the internet: malware, social engineering frauds, and phishing sites.
Why You Need A Vpn, And How To Choose The Right One
All your internet traffic is routed through this tunnel to the server, which then sends the traffic off to the public internet as usual. Data returning to your device makes the same trip: from the internet, to the VPN server, through the encrypted connection, and back to your machine.
There are a couple of alternatives out there to set up your own, such as Overview. Doing so is relatively simple, however you'll either need to keep a server or rent one, which is less basic. While there are some efforts to make self-hosted VPNs more available, it's something best left to tinkerers who aspire to get their hands (digitally) unclean.
If you do not like that a business you're currently paying is benefiting from your data or if you have issues about ISPs hoarding detailed information about your activities, a VPN will assist. Not even your ISP can see your web traffic when you use a VPN.VPNs also make it harder for advertisers and others to track you online.
What Is A Vpn & How Does It Work?
When the VPN is active, your true IP address is concealed, and anybody viewing you can just see the IP address of the VPN server. By hiding your real IP address, VPNs reject snoops one tool utilized to identify and track you online. In spite of that, VPNs do not make you fully anonymous online.
Some VPN services include committed anti-virus tools as well, and some antivirus companies now use VPNs. We do not normally check the malware-detecting abilities of VPNs, given that we see VPNs mainly as a privacy service. To deal with the danger of malware, we believe standalone anti-malware softwarewhether it's one you buy or the one that ships with your computerdoes a much better job.
A VPN will conceal the contents of your web traffic from some observers and can make it harder for you to be tracked online. A VPN can, at best, offer just minimal security against the dangers you're most likely to experience on the web: malware, social engineering frauds, and phishing sites.
Table of Contents
- – How Does A Vpn Work? Tutorial For Beginners
- – What Is A Vpn?
- – What Is A Vpn And Why Should You Use One?
- – What Is A Business Vpn? │ Business Vpn Uses A...
- – What Is A Vpn? Virtual Private Network Tutorial
- – What Is A Vpn And How Does It Work?
- – Why You Need A Vpn, And How To Choose The Ri...
- – What Is A Vpn & How Does It Work?
Latest Posts
10 Best Vpn Services For 2023 - Top Vpns Compared
Best Vpn Companies: Protect Yourself Online
10 Best Vpn Services For Startups 2023 - Truic
More
Latest Posts
10 Best Vpn Services For 2023 - Top Vpns Compared
Best Vpn Companies: Protect Yourself Online
10 Best Vpn Services For Startups 2023 - Truic